
Security 4 Nø0bs — Recon Essentials
Security 4 Nø0bs — Recon Essentials
A high-level discussion on reconnaissance, footprinting, and more

Hola Friends,
If you’re like me, just starting out, a critical resource to know is the Penetration Testing Execution Standard¹ (PTES) which is the foundation for this series. If you’ve never heard of it, or need a refresher, please visit the link below.
So far in this series, we’ve covered the important PTES pre-engagement steps for scope, rules of engagement, and obtaining permission to proceed. We covered the basics of risk assessment, and even discussed what we mean by testing in the first place. We now have a foundation to work with.
In this post we’ll be discussing my favorite step of the PTES: Information Gathering aka, Reconnaissance. Furthermore, we will take a more hands-on approach as we highlight the main points of reconnaissance.
Assignment — Altoro Mutual
Website — http://demo.testfire.net/
Scope — Conduct a “black box” security assessment (penetration test) of Altoro Mutual — A Banking Application. The Client has tasked you — the Security Analyst — with conducting the assessment. You’ve been debriefed on scope and ROE, and have been given clear and expressed permission to conduct a full assessment of their site.
All you’ve been told is that they have developed a series of new features and want to ensure they have been disciplined with secure code best practices. Their QA team has conducted rigorous testing and found no regressions. All features are operating at optimal levels across all browsers and they’ve signed off on deployment to the production environment.
As the Security Analyst, you’ve been given a list of endpoints, the primary domain (url), and not much else. The client has expressed their desire for you to behave as an attacker would, with as little information to work with as possible, to maximize the most optimal approach to testing. Great news!
Fire up your Kali environment and let’s get to work!
Why Recon?
As a Security Analyst you have your target and instructions to act as an attacker. In essence, be “purposefully evil.” So your first step is to gather as much information about your target. The recon step answers questions like, how does this work? what does this do? who does this app serve?
PTES defines a series of levels of information necessary to what is most relevant to the mission: looking for security vulnerabilities.
Below is a sample of tools you can use for automating information gathering:
- Site Report²— a quick and easy means of obtaining high-level information that can be useful for obtaining additional information like hosting services, IP addresses, and tech stack.
- Sites like ExploitDB and CVE.org are essential to obtaining potential exploits for the discovered tech stack in use. A more comprehensive investigation might include any looking for dependencies being used that have their own vulnerabilities. Supply chain attacks, anyone!
- Wappalyzer is a browser extension that will provide additional information regarding the tech stack in use.
We visit Altoro Mutual and we click around for clues on how it works, who might be the users, and how expansive the attack surface is. We see a myriad of services being offered; links to respective pages. They have a section for return users, with services like loans, deposits, credit lines, and other financial instruments. Interesting!
Further down we see they service small business. Whom might these businesses be? What might we be able to learn from these business? So many clues …
OSINT
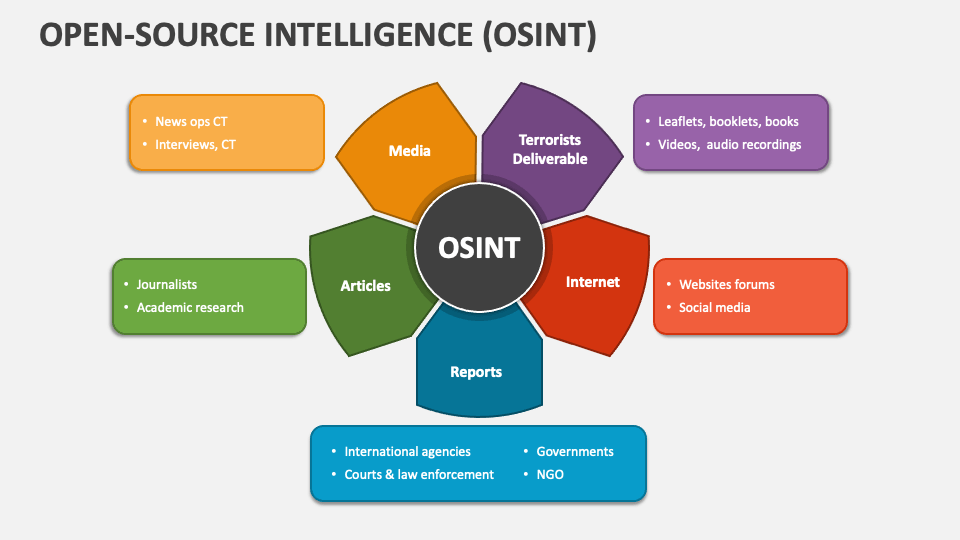
Open Source Intelligence is another super-useful step in the information gathering phase of the test effort. News reports and social media posts can be useful tools that may potentially inadvertently yield sensitive information. It’s not uncommon to leverage the CEO’s facebook page to discover their favorite pet which may coincidentally be their password.
As the Security Analyst on the project, you have to be judicious with your time. If sufficient time allows for OSINT, by all means take advantage of it to the best of your abilities. More often than not, you’re under a time constraint and every hour is precious.
Information Gathering

In this section, a number of items should be written up to show the Client the extent of public and private information available through the execution of the Intelligence gathering phase of PTES. At a minimum, the results identified should be presented in 4 basic categories:
Passive Intelligence
Intelligence gathered from indirect analysis such as DNS, Google dorking³ for IP/infrastructure related information.
The information we get from passive intelligence will help yield the kind of results that inform us depth and breadth of the site.
Active Intelligence
As an anlyst you will perform tasks such as infrastructure mapping, port scanning, and architecture assessment and other activities. Techniques might include (not a comprehensive list):
- Enumeration of the target to discover urls that are not necessarily customer-facing with a tool like feroxbuster
- Using Ping — a simple terminal command used to determine the state of the target-under-test — ping
- Performing host discovery with nmap — nmap -sV -oA initial_scan
- Using NSLook up — nslookup {target url} — another terminal command that will provide useful information for domain name services in use.
- Fingerprint the webserver with netcat — nc {target url} 80
- Perform Banner grab w. Netcat — nc -nv
- Learn more about the open ports — nmap -sC -oA -p 22,80 script_scan
- Look for metafiles like sitemap.xml, robots.txt, and security.txt
- Directory Brute Force w. Gobuster — gobuster dir -u -w /usr/share/dirb/wordlists/common.txt
Our report should show how we obtained this information (as the need warrants).
Corporate Intelligence
Information about the structure of the organization, business units, market share, vertical, and other corporate functions should be mapped to both business process and the previously identified physical assets being tested.
Knowing who is in charge might help us determine how we might be able to conduct social engineering or phishing scams. Let’s keep digging!
Personnel Intelligence
Any and all information found during the intelligence collection phase which maps users to the client organization. This section should show the techniques used to harvest intelligence such as public/private employee depots, mail repositories, org charts and other items leading to the connection of employee/company.
Our report should also show our understanding of the organization and how we obtained that information. This might always be necessary, but if the client feels like exposure of this information is a risk, even a low one, it might be worth fixing.
Conclusion
I find the recon step the most enjoyable step of the penetration test as it helps us frame the boundaries of what we know about the client and the approaches to take for testing.
The more we learn about the attack surface, and potential vulnerabilities, the better our testing will be, and the greater the value our efforts will add to the project.
The recon step can be tedious and time-consuming at times, but I’ve worked to automate as much of the process as I could to free up time. The end result is a critical and efficient completion of the first phase in our pen testing.
For Altoro Mutual, we obtained the IPs, the Urls, and a map of the attack surface. Next week, we’ll discuss Threat Modeling.
Until next time …
ciao for now
