
Creating a Realistic Performance Test Using the Refresh Token Endpoint in JMeter
Published on February 26, 2024
When conducting performance testing, it's vital to simulate user behavior as accurately as possible. A common scenario involves testing a JWT-protected API over an extended period, which presents a challenge when the token has a short expiration time. In this blog post, we'll discuss how to create a realistic test in JMeter for an API that retrieves invoices and is protected by JWT, focusing on the efficient use of the refresh token mechanism.
The Challenge:
We aim to test an API endpoint (/invoices) that requires a valid JWT token. This token is initially obtained via a /users/login endpoint but only remains valid for 300 seconds. We'll use the /users/refresh endpoint to avoid frequent logins to renew the token.
JMeter Setup:
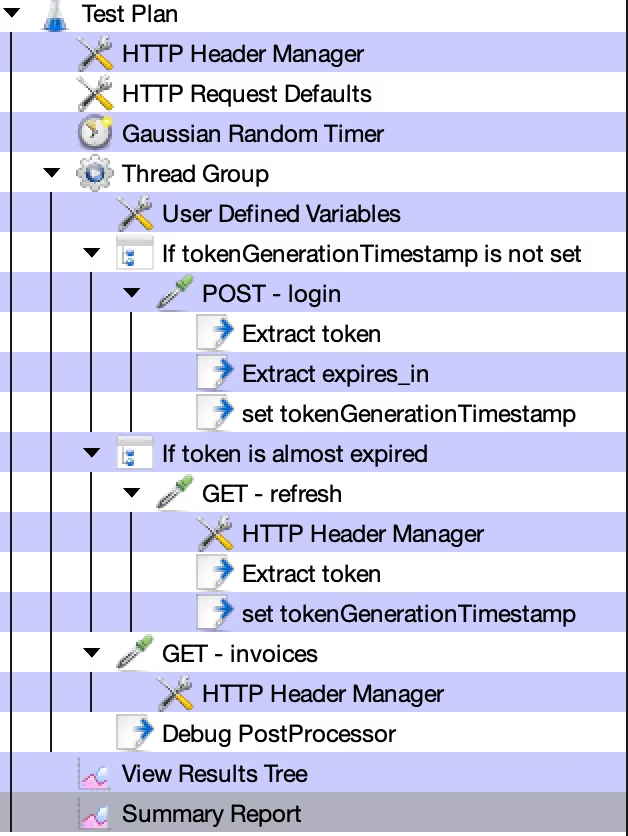
Here are the steps to set up this test in JMeter:-
Checking Token Generation Timestamp:
- Use an If Controller with a JEXL3 script
${__jexl3(${tokenGenerationTimestamp} == 0,)}to check if tokenGenerationTimestamp is set. This variable holds the timestamp of the last token generation.
- Use an If Controller with a JEXL3 script
-
Initial Login and Token Extraction:
- Inside the If Controller body, if tokenGenerationTimestamp is not set, make a POST request to
/users/login. - Extract the token and expires_in values from the login response.
- Set tokenGenerationTimestamp using
vars.put("tokenGenerationTimestamp", "${__time(,)}"). This records the time of token acquisition.
- Inside the If Controller body, if tokenGenerationTimestamp is not set, make a POST request to
-
Checking Token Expiration:
- Use another If Controller to check if the token is close to expiring with
${__jexl3((${__time(,)} - ${tokenGenerationTimestamp}) > (${EXPIRES_IN} * 900))}. Here, EXPIRES_IN is the duration in seconds and 900 represents 90% of the expiration time.
- Use another If Controller to check if the token is close to expiring with
-
Refreshing the Token:
- If the token is almost expired, send a GET request to
/users/refreshto obtain a new token. - Extract the new token and update tokenGenerationTimestamp as before.
- If the token is almost expired, send a GET request to
-
Performing the Invoice Retrieval:
- Now, you can make the GET request to
/invoices. - Set the
Authorizationheader toBearer ${TOKEN}to pass the JWT token.
- Now, you can make the GET request to
Expected Test Behavior:
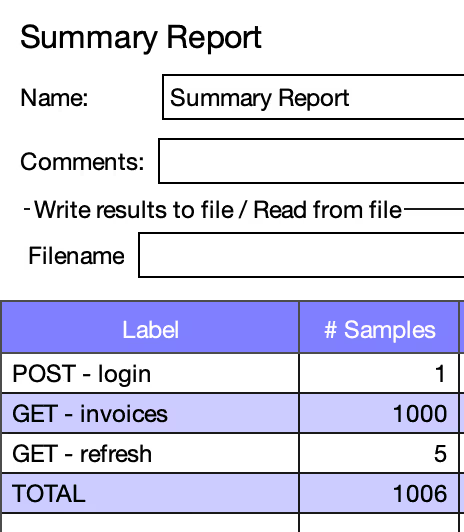
- POST /users/login is called only once at the beginning.
- GET /invoices is called multiple times, simulating the continuous use of the API over time.
- GET /users/refresh is called periodically, just before the token expires, reducing the load on the login endpoint.
Why This Approach?
Using the refresh token endpoint instead of repeatedly hitting/users/login more accurately simulates real user behavior. In real-world scenarios, applications don't login each time they need to access a JWT-protected resource; they refresh the token when needed. This approach also helps in identifying potential issues with the token refresh mechanism and ensures the stability and performance of the API under prolonged use.
